
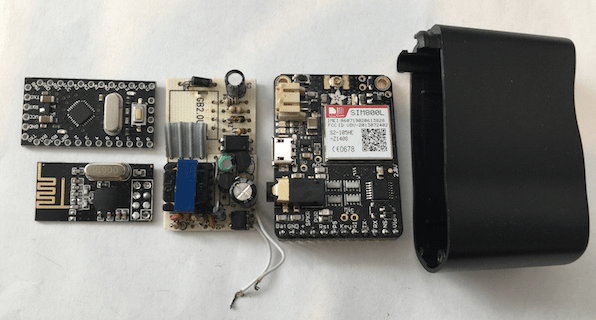
Alas, it’s not Ben’s charger. Hell, it’s not a charger at all. It’s actually a little spy device disguisedas a phone charger, capable of sniffing out every key you type on that wireless keyboard on your desk. Oh, and it can send the stuff it picks up straight to the eavesdropper’s phone. Oh! Oh! And it’ll keep working even if you unplug it — it only pretends to turn off.
That little box up top is built by Samy Kamkar (Yeah — the same Samy who built the self-titled worm that ravaged Myspace back in the day, and who built that crazy hands-free hacking necklace a few weeks back) who has dubbed it the “KeySweeper.”
Before you panic and throw your keyboard in the trash, here is the good news: This specific device only affects certain wireless keyboards. Most notably, Microsoft-branded wireless keyboards. We’re still trying to dig up a more exhaustive list — but for now, let “Microsoft wireless keyboard” be your caution sign.
In a statement, Microsoft notes that it only affects its 2.4 Ghz (not Bluetooth) keyboards released before July 2011 (Update: See the bottom of this post for a note on this from Samy, the man behind the hack). Even if it’s “only” older keyboards, remember: outside of the gamer crowd, most people don’t update their keyboards very often.
Here’s some of the crazier stuff KeySweeper can do:
- Sniff out keystrokes as you type them.
- If it detects certain keystrokes (like “TopSecretWebsite.com”), it can grab the chunk of text that follows (like your username and password) and send it over SMS to whoever planted the device.
- Store keystroke logs on the device itself. These logs can be extracted from the device by hardwired USB, or by putting a second KeySweeper device within range of the first (like, say, an outlet on the other side of the wall).
- When plugged in, it grabs its power from the wall.
- When unplugged from the wall by an abnormally suspicious bystander, it looks like it powers down — but it actually just switches to battery power. Logging/sending continues. Naaaasty.
On the upside, most brand-name wireless keyboards sold today use encryption methods that are a bit tougher to crack. Logitech, for example, uses 128-bit AES on all of its wireless stuff (see page 6 of this doc for reference).
Samy estimates that each unit would cost $10 to $80 to build, depending on what sort of features you want (ditching the SMS support, for example, brings it down by about $45) — but is quick to note that he’s not actually selling these.
You can (and should!) read Samy’s full breakdown of the project over here.
Update: While Microsoft says only keyboards before July 2011 are impacted, Samy shot me a note to point out that said keyboards are still on sale and seemingly manufactured:
Just wanted to mention — while Microsoft states it only affects keyboards before 2011, the vulnerable keyboards are *still* being manufactured and sold today, even from Microsoft’s own web site and major retailers like Best Buy.I purchased the vulnerable keyboard brand new from Best Buy just last month, and the date next to the serial number says “07/2014″



No comments:
Post a Comment
Please leave a comment if you can.